
NIS2 in the critical infrastructure
Discover how the NIS2 directive is revolutionizing the security of critical infrastructures. Find out what measures are necessary to effectively counter cyber threats and ensure the reliability and trustworthiness of your systems.
NIS2
Security and resilience for the future
We will show you how a structured ISMS can help you comply with the new EU directive, combat cyber threats and ensure the reliability of critical infrastructure.
In the era of advancing digital networking, critical infrastructures form the foundation of our modern civilization. Sectors such as energy, healthcare and digital communication are essential for the continuity of daily life and the stability of the economy. The implementation of the NIS2 (Network and Information Security 2) directive marks a significant evolution in cybersecurity requirements for these vital systems.
NIS2 tightens existing security standards and obliges organizations to take a proactive stance towards the escalating cyber threat landscape. This article focuses on the strategic relevance of the NIS2 directive, the specific operational and technical challenges in the context of critical infrastructures and the measures that are absolutely necessary to ensure the security and resilience of these system-relevant facilities.
Protect your company
These sectors fall under critical infrastructure
Energy
Includes companies and infrastructures in the electricity, gas and oil supply sectors. Their failure would have serious consequences for the economy, public safety and the functioning of other critical sectors. Investment in cyber security is essential. .
Transport
Includes transportation and logistics networks in aviation, shipping, rail and road transport. Cyber attacks could lead to chaos, accidents and significant economic damage. Resilient systems are crucial.
Public administration
Refers to government and administrative systems at all levels that are responsible for the provision of public services. Cyber attacks can disrupt government functions and undermine the trust of citizens. High security standards are essential.
Health
Includes healthcare providers and infrastructure, including hospitals and health information systems. Cyber attacks put patient data, medical devices and care at risk. Protecting human lives is a top priority.
Banking
Includes financial institutions and banks that offer basic financial services. Cyber threats target customer data, financial stability and trust in the system. Robust security measures are mandatory.
Financial market infrastructures
Affects systems and infrastructures that are essential for the smooth operation of financial markets (e.g. stock exchanges, clearing houses). Cyber incidents could have a global financial impact. The highest security standards are required.
Digital infrastructure
Affects companies and infrastructures that provide digital services, including cloud services and data centers. As the foundation of the digital economy, they are prime targets for cyberattacks. High availability and security are crucial.
ICT service management
Includes companies that manage information and communication technologies for other companies. Vulnerabilities in these services can have far-reaching consequences for their customers. Proactive security measures are essential.
Digital providers
Includes companies that provide digital services for end users (e.g. social networks, search engines). Cyber attacks can affect millions of users. High security standards and resilience are essential.
Chemical industry
Affects companies that manufacture, process and distribute chemical substances. Cyber attacks could lead to dangerous production downtimes or acts of sabotage. Strict security measures are essential.
Food Industry
Includes companies and infrastructures along the food chain. Cyberattacks could jeopardize security of supply and affect public health. Resilient systems are essential.
Manufacturing
Refers to companies involved in the production and processing of goods. Cyber attacks can disrupt production processes and interrupt supply chains. Comprehensive security concepts are necessary.
Waste management
Includes systems and infrastructures responsible for waste disposal and recycling. Cyber incidents could lead to environmental hazards and disruption to public order. Secure operations are crucial.
Drinking water
Refers to systems and infrastructure responsible for the provision of clean drinking water. Cyber manipulation could affect water quality and endanger public health. Strict security precautions are necessary.
Waste water
Includes systems and infrastructures responsible for wastewater disposal and treatment. Cyber attacks could lead to environmental pollution and health risks. Reliable and secure systems are essential.
Postal and courier services
Refers to companies that offer postal and courier services. These are essential for the movement of goods and communication. Cyber attacks could disrupt supply chains. Continuous security improvements are necessary.
Space
Includes infrastructures and systems related to the space industry. These are critical for communication, navigation, earth observation and security. Cyber resilience is of strategic importance.
Research
Refers to organizations that are active in scientific research and whose work is important for national security or the public interest. The loss of sensitive research data would have serious consequences. Strict protective measures are required.
If you would like more detailed information on the NIS2 law, we recommend our NIS2 AI Co-Consultant or refer to the current NIS2 EU Regulation or the draft law of the Austrian Federal Government.
ISMS Live
Take a look at our ISMS in action
As the person in charge of information security, one of the challenges you face is managing risks quickly and efficiently without losing sight of the big picture.
This is exactly where we come in – not at some point, but now. See for yourself in our short video or the guided tour on Webinar Geek.
An example
The invisible danger to your energy supply
In this scenario, we consider a fictitious energy supply company that is responsible for providing electricity to millions of households and businesses.
A flickering light, production downtime, the failure of critical systems – scenarios that seem unimaginable in modern energy supply. But behind the facade of smooth processes lurks an ever-growing threat that can plunge your entire infrastructure into the abyss: Cyberattacks.
Your company that is responsible for the reliable energy supply of an entire region. Every day, your systems control complex networks, optimize loads and secure the flow of electricity and heat. But what happens when this invisible digital enemy strikes? When cyber criminals infiltrate your control systems, encrypt your data or even take control of your systems?
The ransomware trap
A careless click, an infected email – and suddenly your most important data and control systems are blocked. The demand: a high ransom to regain control. But even with payment, uncertainty remains and trust is permanently shaken.
OT attacks
Attacks on your industrial control systems (ICS) and operational technologies (OT) are not aimed at data, but at the physical processes. Tampering could lead to unnoticed damage to systems, malfunctions or even dangerous malfunctions, the extent of which is unpredictable.
Social Engineering
Your employees are often the weakest link in the chain. Perfidious phishing emails or social engineering tactics can tempt them to unknowingly introduce malware or disclose sensitive access data – the door opener for devastating attacks.
Failure of critical infrastructure
A successful cyber attack can lead to widespread and long-lasting power outages. Hospitals, transport systems, communication networks – the entire foundation of our modern society is shaken.
Reputational damage & financial losses
A cyber incident on your scale inevitably results in massive negative headlines. The trust of customers, partners and the public dwindles, which can lead to long-term financial losses and irreparable damage to your image.
Regulation & Liability
Legal requirements and guidelines for cyber security in critical infrastructure are becoming increasingly strict. Failure to comply can lead to severe penalties, fines and even personal liability for those responsible.
Take back control of your cyber security with 4conform ENTERPRISE ISMS. Our comprehensive solution helps you build a robust and customized information security management system that detects threats early, protects your critical infrastructure and helps you meet complex regulatory requirements – to keep the lights on safely.
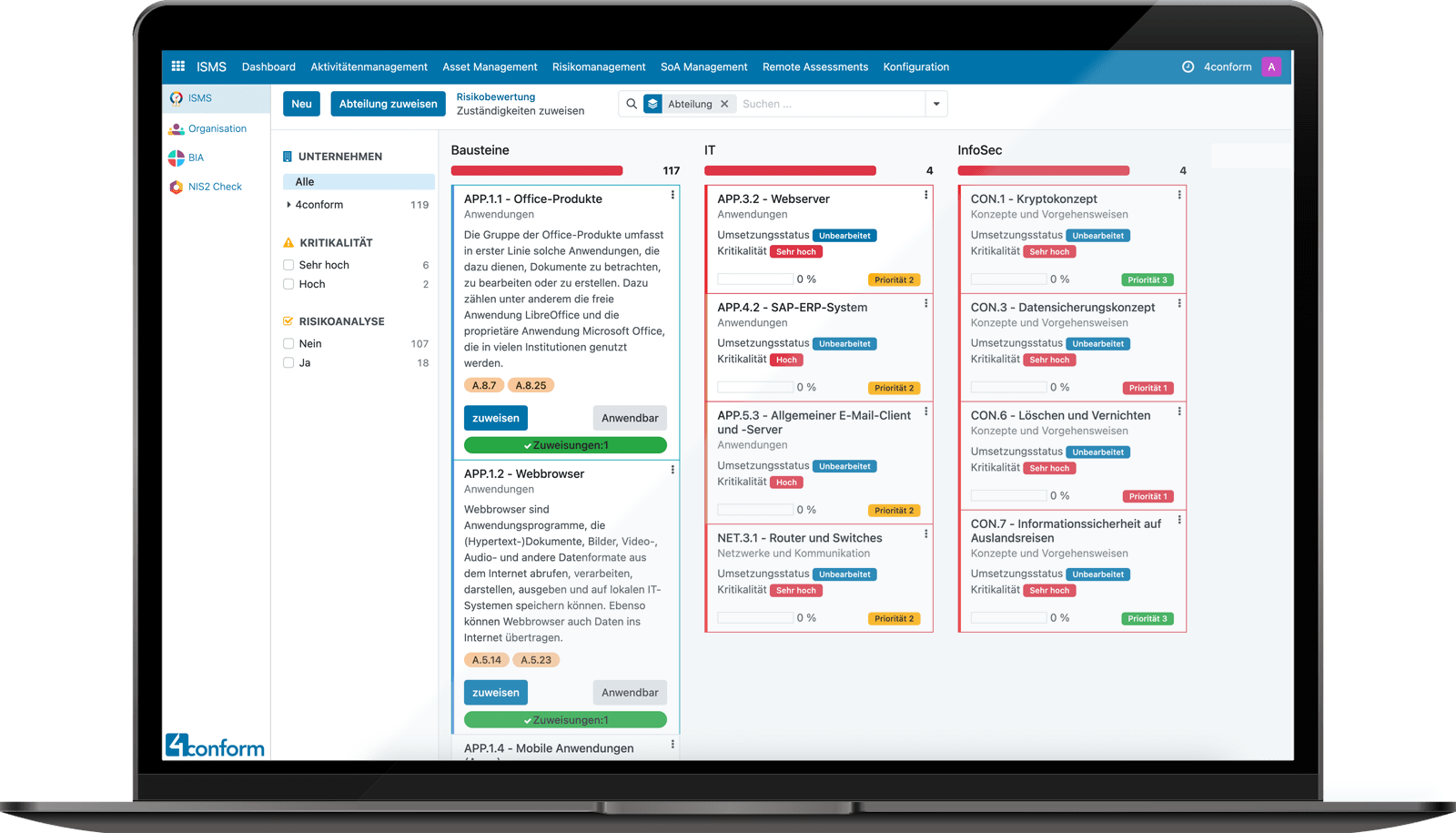
Keep an eye on all departments and their risks.
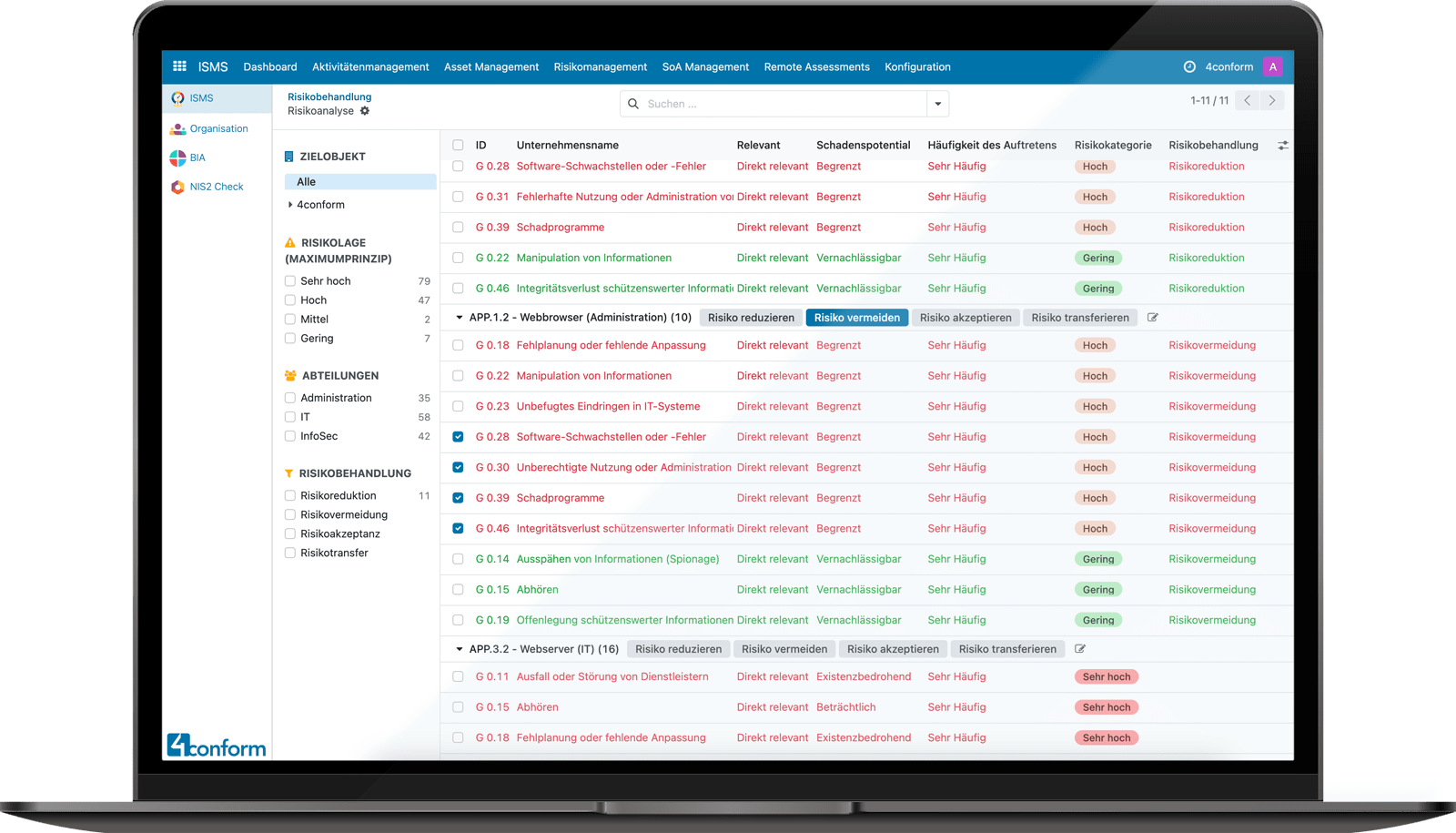
Risk treatment of all hazards for your company.
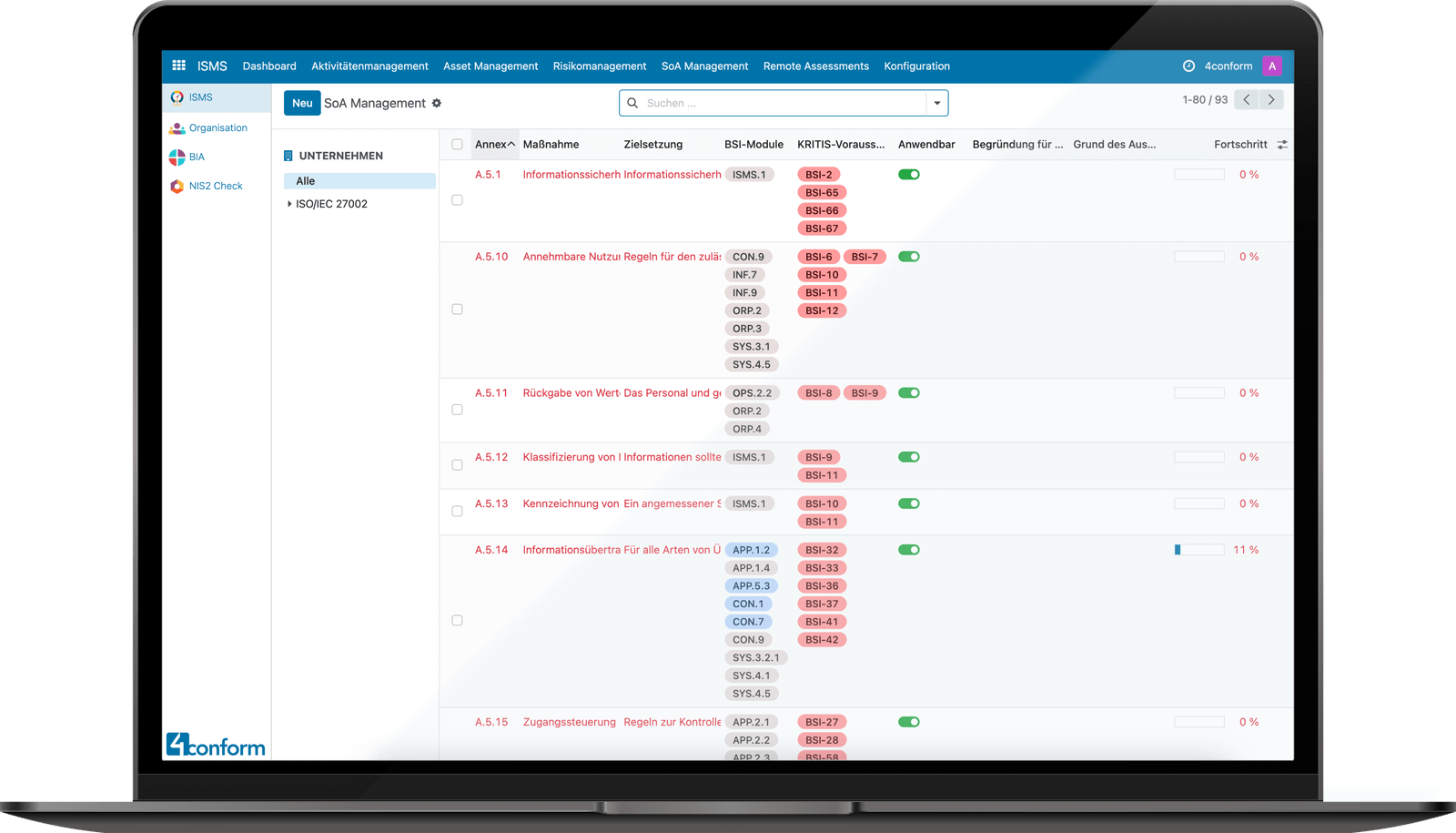
Statement of applicability in 4conform ENTERPRISE ISMS als Checkliste.
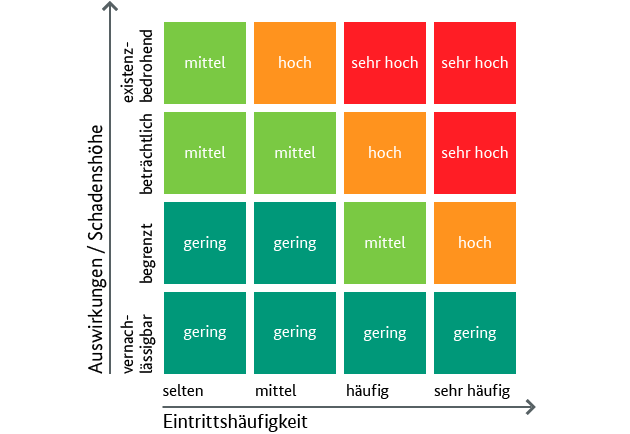
Classify your risks with the help of the BSI risk matrix.
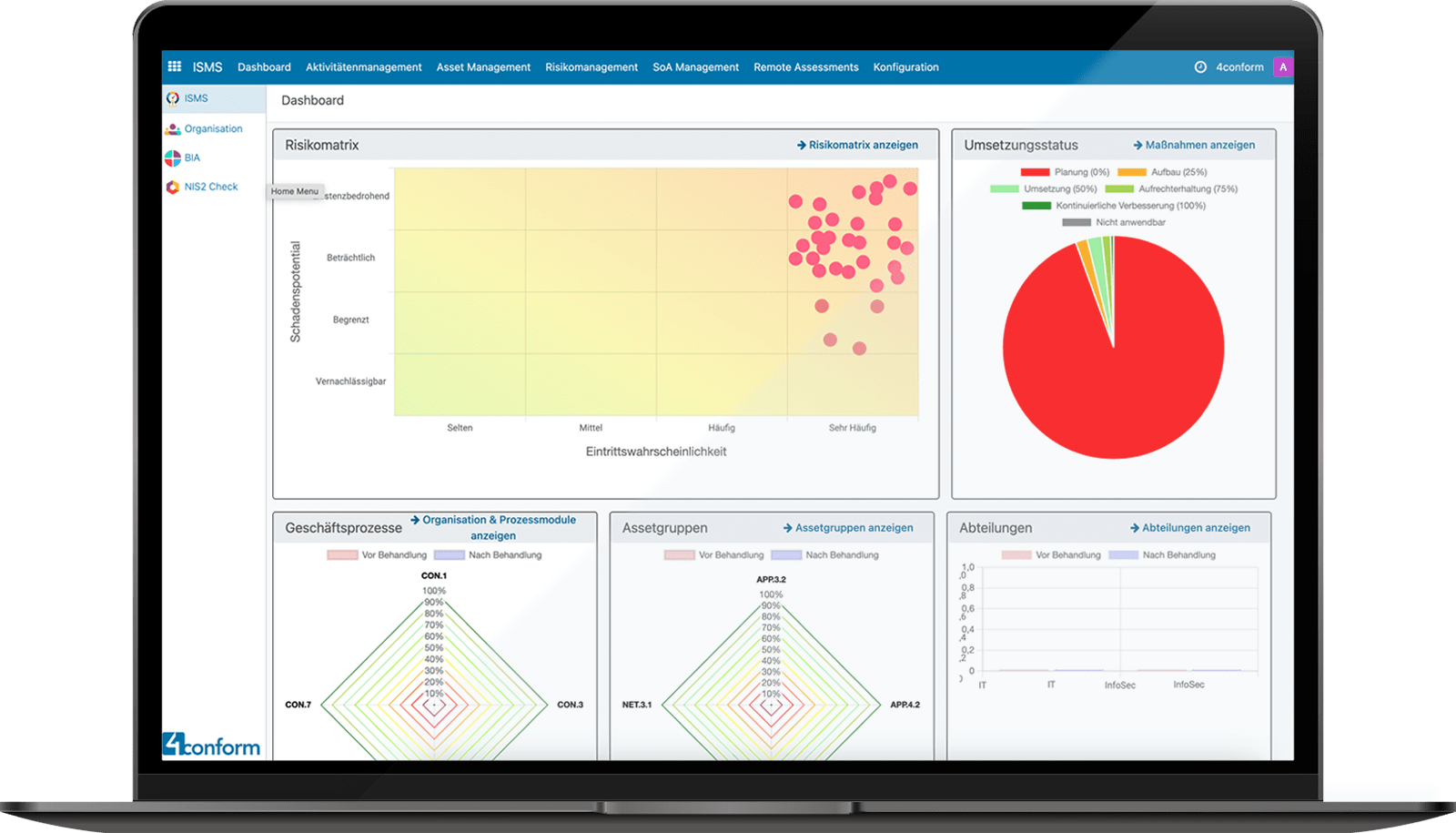
The risk matrix in the 4conform ENTERPRISE ISMS dashboard
Information security
How can our ISMS help?
A structured information security management system (ISMS) is essential for companies directly affected by NIS2. It is essential for those responsible to effectively protect their critical infrastructures from cyber threats.
The 4conform ENTERPRISE ISMS enables, for example, the securing of control systems (ICS/OT), compliance with industry-specific regulations, precise risk management for targeted attacks and a rapid response to security incidents. With an ISMS, you improve your organizational security, ensure data integrity and availability and increase resilience.
This will ultimately ensure security of supply for the economy and society. Invest in an ISMS to make your energy infrastructure future-proof.
BSI basic protection included
Start your ISMS without detours! Our 4conform ENTERPRISE ISMS software contains all relevant BSI basic protection modules with the corresponding measures.
This means you can get started right away. Rely on a proven solution that saves you time, resources and headaches. Secure your company with an ISMS that has been developed by experts and meets the highest standards.
What benefits does an ISMS offer?
4conform ENTERPRISE ISMS is used specifically to make managing your information security easier and more efficient. It serves as a central platform to support processes relating to information security, risk and compliance management.
What our customers in the energy industry say
“The BSI approach of the 4conform Enterprise ISMS convinced us immediately and makes the complex topic of risk assessment as simple as possible. The distributed assessment and integration of other departments is implemented optimally. The response times and service at 4conform clearly stand out from other providers.”
Energiewerke Wels
Electricity & energy supplier

Data protection
How can our DSMS help you?
For companies that are directly affected by NIS2, a comprehensive data protection management system (DSMS) is a must in order to ensure the security and integrity of sensitive data. 4conform offers a customized DSMS specifically for this area. Our ENTERPRISE DSMS ensures that all data processing procedures comply with legal requirements and that the privacy of data subjects is protected.
A DSMS supports the critical infrastructure in strengthening the trust of stakeholders and minimizing legal risks. By implementing a DSMS, organizations in the critical infrastructure can not only ensure compliance, but also protect their reputation and ensure the reliability of their systems. This is crucial to ensure the continuity and security of services that are central to the functioning of society and the economy.
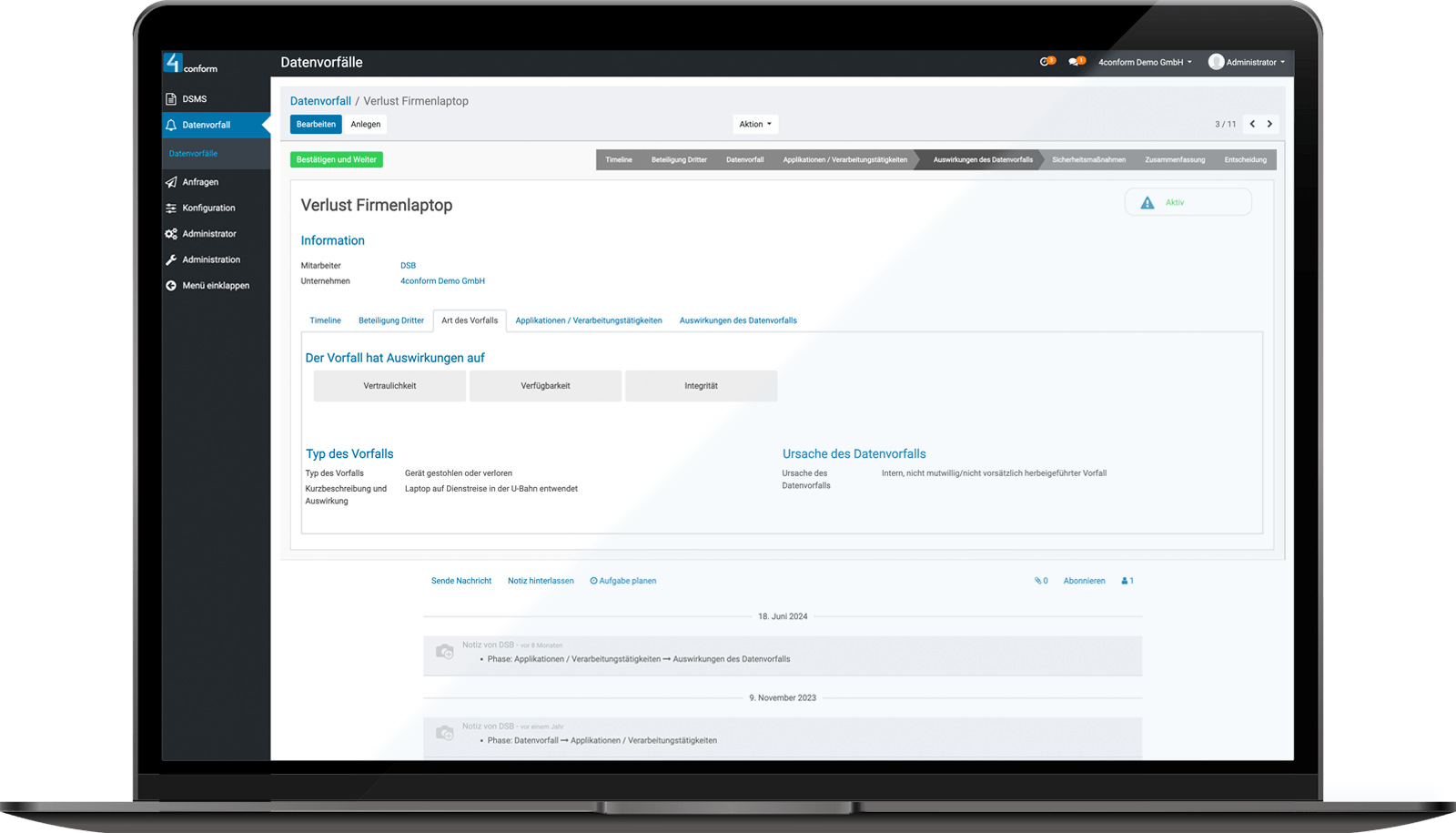
Process data incidents easily and in compliance with the law in ENTERPRISE DSMS.
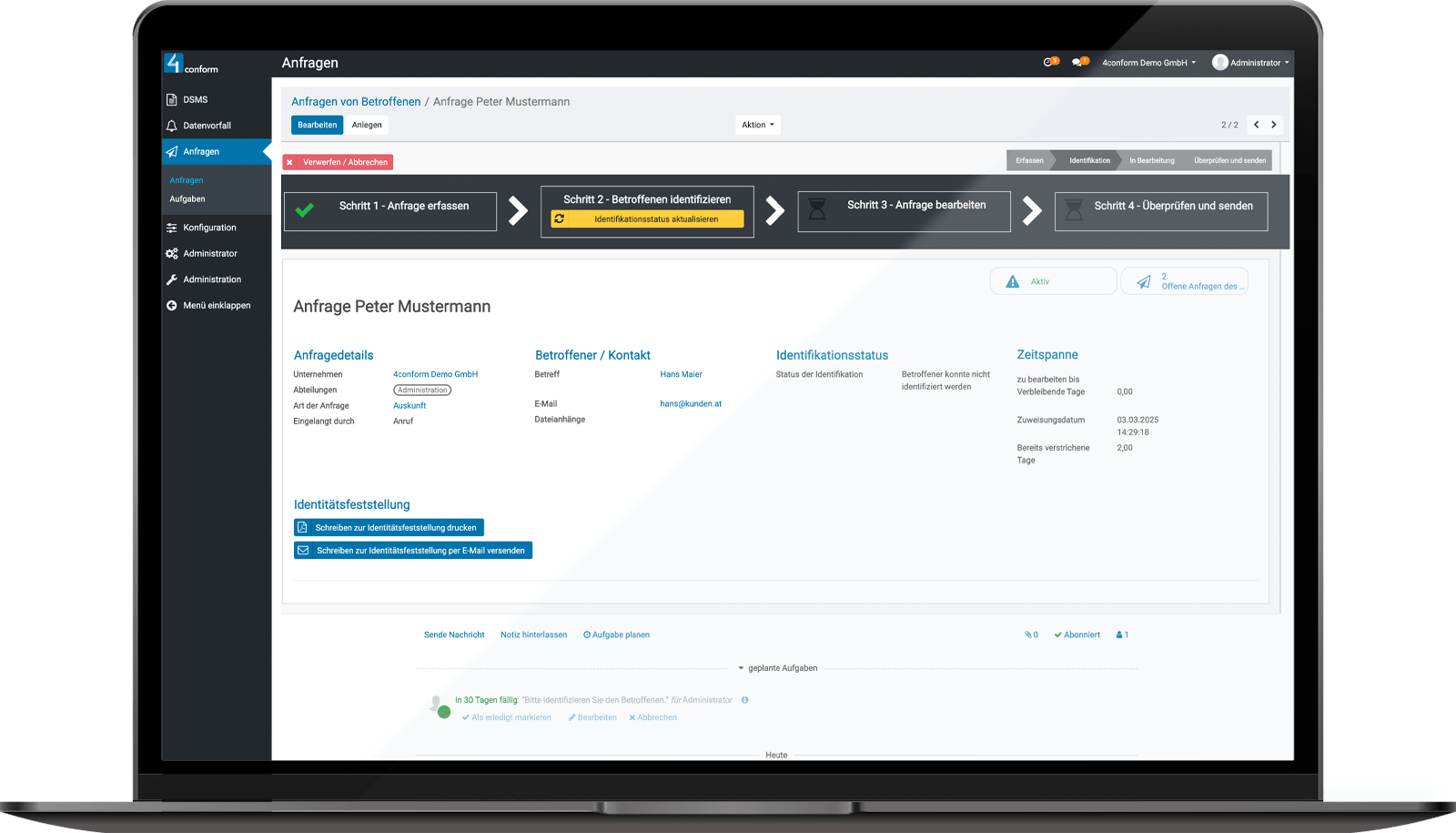
Manage and process your data subject requests in accordance with the legal requirements.
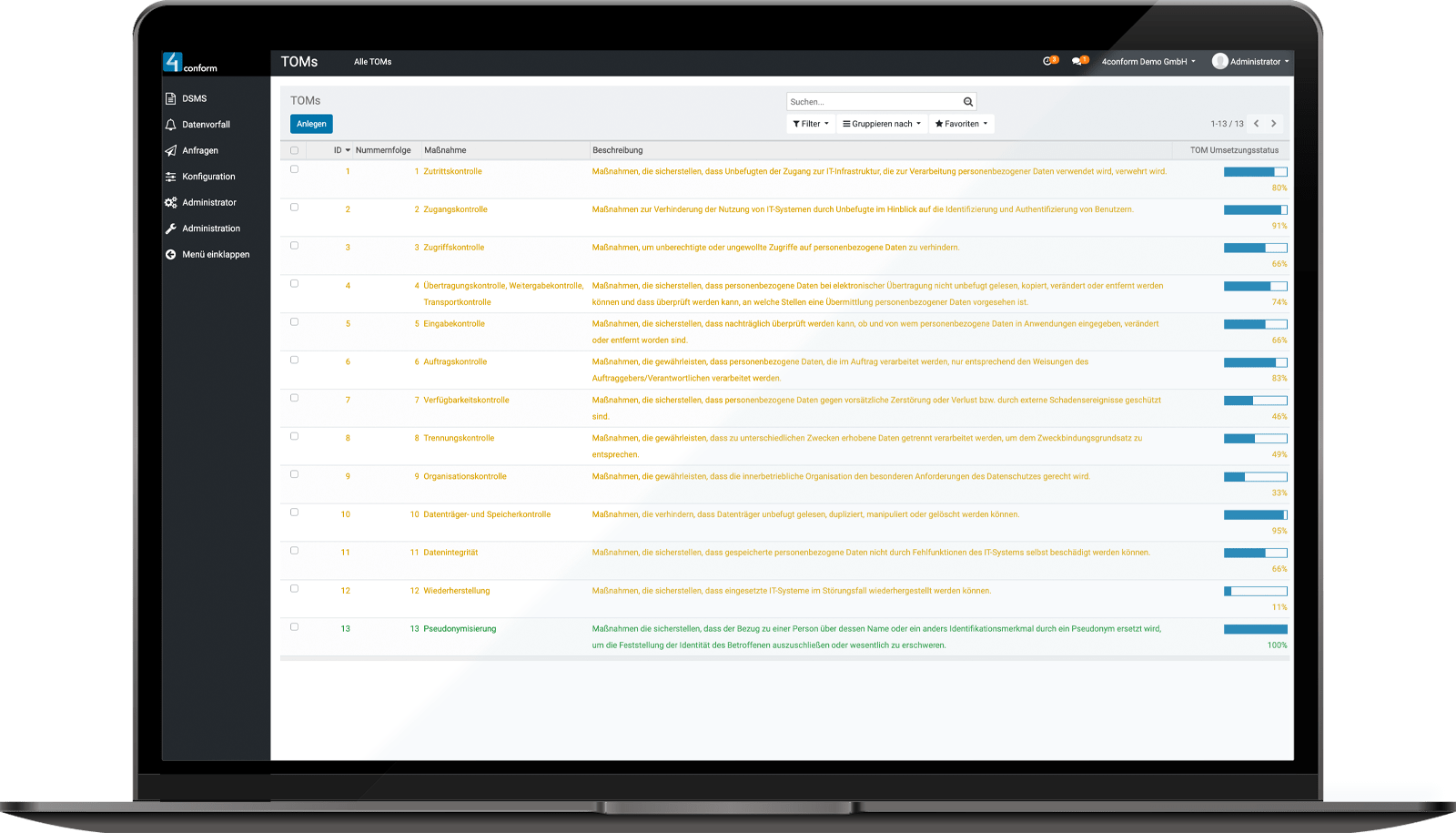
Map out your technical and organizational measures.
DSMS Live
Take a look at our DSMS in action
Book a demo now and find out how you can efficiently ensure the protection of sensitive data and meet legal requirements. In your demo appointment, we will show you how easy it is to integrate data protection into your company. Save your appointment and start into a more secure future!

What benefits does a DSMS offer?
Our ENTERPRISE DSMS software (data protection management system) is primarily used to ensure the protection and management of data in an organization. It focuses on compliance with data protection and data security regulations and the prevention of data breaches.
“The NIS2 directive marks a turning point in cyber security that directly affects us all. We therefore want to support our customers in implementing the new requirements. At the same time, we are directly challenged to develop robust and innovative solutions that not only meet the legal requirements, but also ensure the security and integrity of our digital infrastructure. Together, we can strengthen the resilience of our critical systems and shape a secure future.”

Full security with 4conform
Information and data security is a complex topic. But it doesn’t have to be complicated. Get to know our smart GRC and information security solutions and arrange a non-binding initial consultation.












