
Why small and medium-sized businesses should prepare for NIS2
NIS2 has been around since October 2024, and small and medium-sized businesses also need to act. Cyber attacks are no longer just a threat to large corporations. Don’t ignore the risks! We show you how to make your SME fit for NIS2 – simply and clearly.
NIS2
Why small businesses also need to act now
We will show you how you can master the requirements of the new EU directive with a structured information security management system (ISMS) and effectively protect your SME from cyber attacks.
Seit 17. Oktober 2024 ist die Neuauflage NIS2 verpflichtend umzusetzen. Obwohl viele Länder in der europäischen Union das geltende EU-Gesetz noch nicht in das lokale Gesetz übertragen haben, ist es nur eine Frage der Zeit. NIS2 rückt näher und bringt für KMUs neue Herausforderungen mit sich. Cyberangriffe sind längst keine Bedrohung mehr, die nur Großkonzerne betrifft.
Small and medium-sized companies are also the focus of cyber criminals. This makes it all the more important to arm yourself now and strengthen your own IT security. An ISMS can help to maintain an overview and efficiently implement the requirements of NIS2. This is because a well-structured ISMS makes it possible to identify risks, implement security measures and demonstrate compliance with the directive. This protects your company from cyber attacks, avoids high fines and strengthens the trust of your customers.
Protect your company
9 threats to your business
Ransomware attacks
Cyber criminals encrypt your data and demand a ransom. Such an attack can lead to business interruptions, financial losses and reputational damage. SMEs are often seen as easy targets, which increases the danger.
Phishing attacks
Employees are tricked into disclosing sensitive data by fake emails or messages. These attacks are often difficult to detect and can lead to data loss and financial damage.
Denial of service attacks (DoS)
The accessibility of your online services is blocked by targeted attacks. This can lead to lost sales and a loss of customer confidence.
Data theft
Customer, employee or business data is stolen and misused. This can lead to legal consequences, reputational damage and the loss of competitive advantages.
Malware (malicious software)
Viruses, Trojans and other malware can infect your systems and damage or steal data. This can lead to considerable damage and business interruptions.
Social Engineering
Employees are manipulated to disclose sensitive information or carry out malicious actions. This can lead to significant security gaps.
Lack of data backup
Missing or inadequate backups can lead to a total failure in the event of data loss. This can threaten the existence of your company.
Internal threats
Dissatisfied employees or former employees can deliberately delete, manipulate or steal data. Internal threats are often underestimated.
Lack of IT security guidelines
Without clear guidelines and processes, your systems and data are inadequately protected. This increases the risk of cyberattacks and data loss.
ISMS Live
Take a look at our ISMS in action
As the person in charge of information security, one of the challenges you face is managing risks quickly and efficiently without losing sight of the big picture.
This is exactly where we come in – not at some point, but now. See for yourself in our short video or the guided tour on Webinar Geek.
Information security
[In-for-ma-ti-on-se-cu-ri-ty], the; noun
Information security refers to the protection of information from unauthorized access, use, disclosure, disruption, modification or destruction. It includes measures and strategies to ensure that information remains confidential, integer and available.
ISO 27001 is an internationally recognized standard for information security management systems (ISMS). It offers a systematic approach to implementing, maintaining and improving information security within an organization.
Confidentiality
Ensuring that information is only accessible to authorized persons or systems. This protects sensitive data from unauthorized access.
Integrity
Ensuring that information is accurate, complete and protected from unauthorized or unintentional modification. This ensures that data remains reliable and accurate.
Availability
Ensuring that authorized users can access the required information at all times. This includes measures to ensure business continuity and minimize downtime.
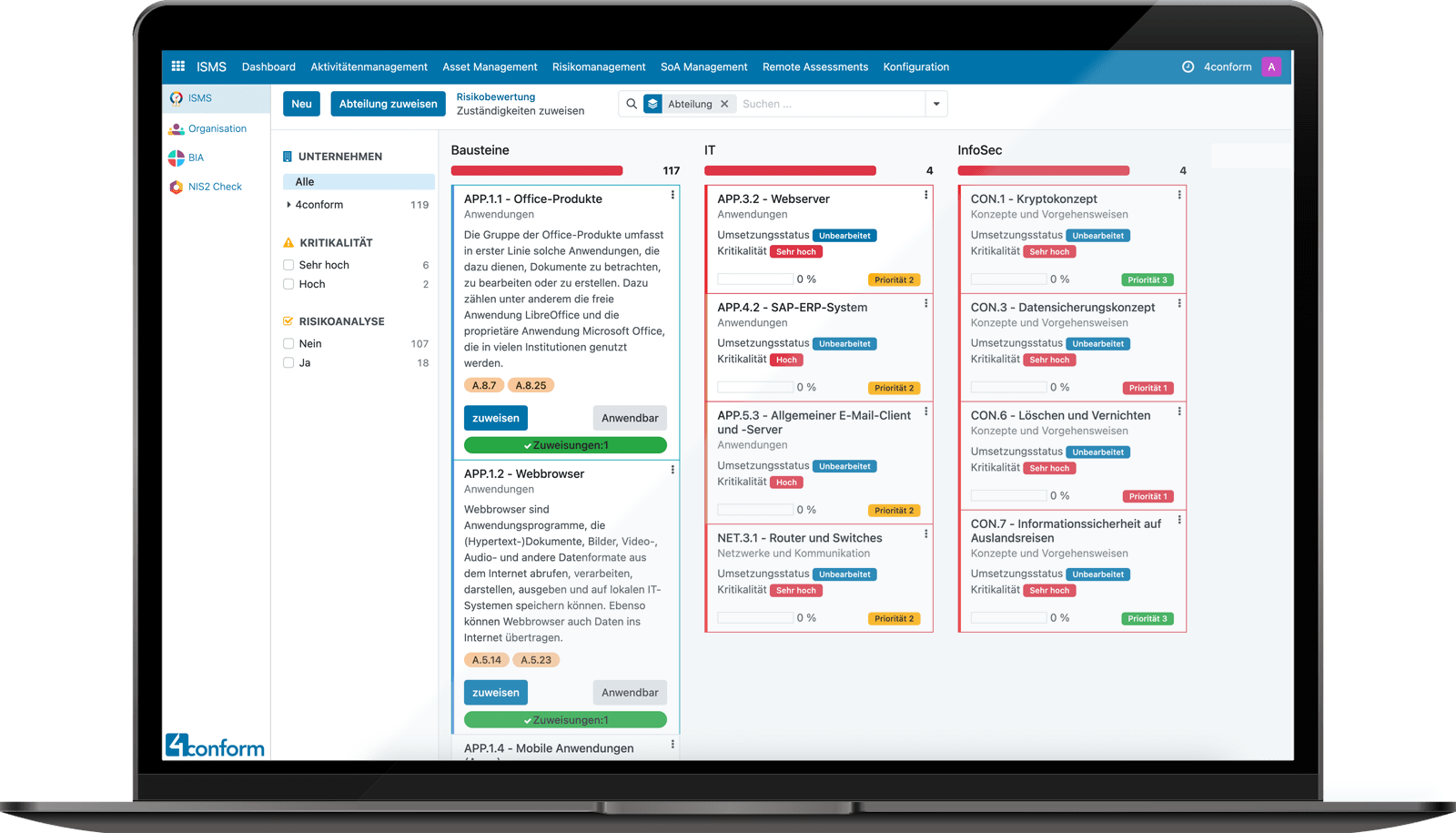
Keep an eye on all departments and their risks.
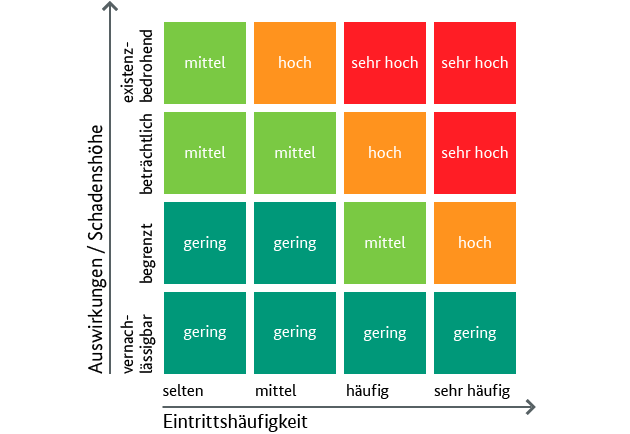
Classify your risks with the help of the BSI risk matrix.
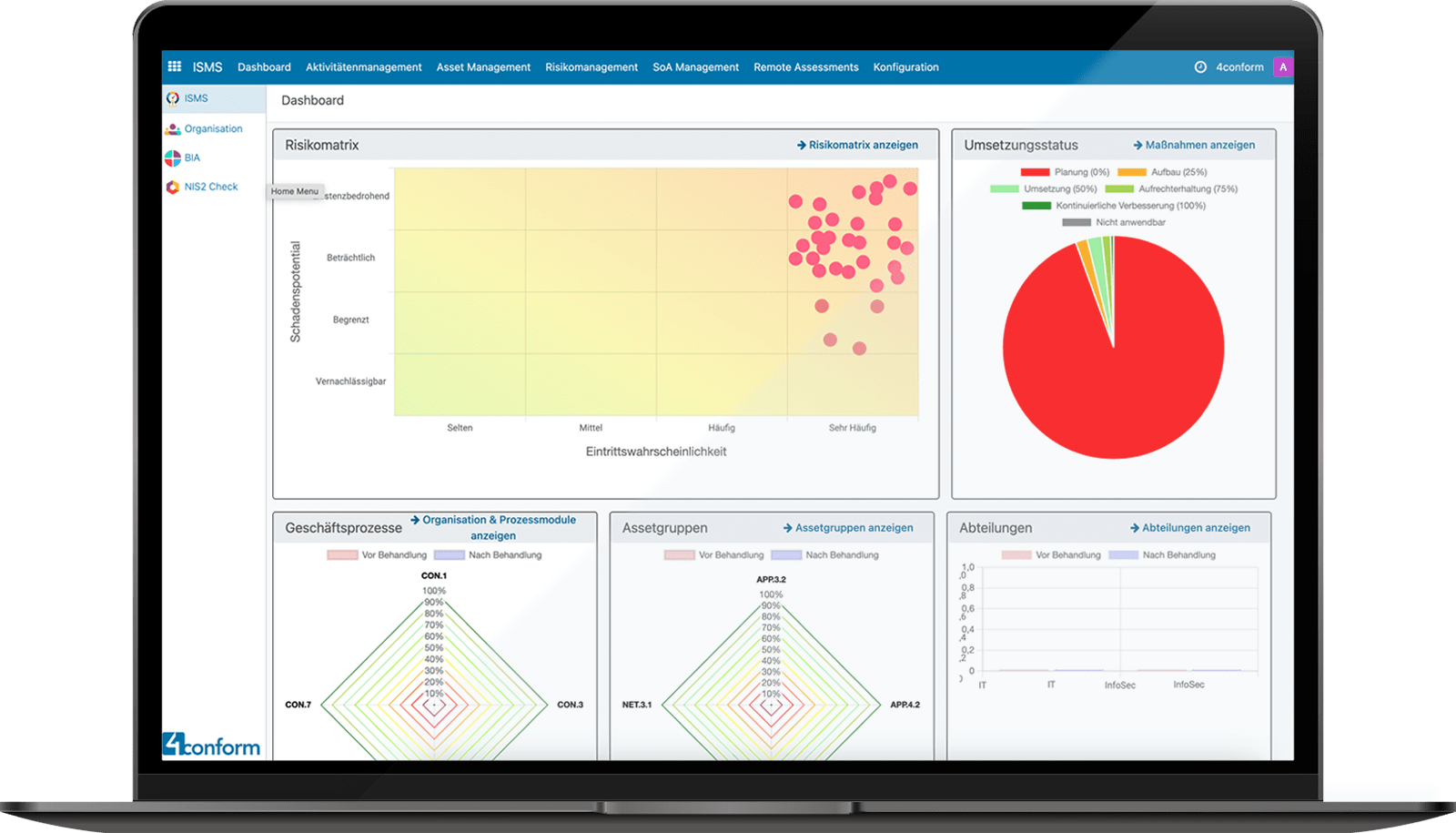
The risk matrix in the 4conform ENTERPRISE ISMS dashboard
Information security
How can our ISMS help?
The security of your data and processes is extremely important for every SME. Our efficient 4conform ENTERPRISE ISMS software helps you to ensure this security. An ISMS is like a safety net that detects risks before they become a problem.
Imagine if you could detect and prevent potential cyberattacks or failures at an early stage – this is exactly what an ISMS helps you to do. In the digital world, where data flows need to run smoothly, this is invaluable.
Protect your company from costly failures and strengthen the trust of your customers. With 4conform, you can maintain an overview and ensure secure, smooth operation.
BSI basic protection included
Start your ISMS without detours! Our 4conform ENTERPRISE ISMS software contains all relevant BSI basic protection modules with the corresponding measures.
This means you can get started right away. Rely on a proven solution that saves you time, resources and headaches. Secure your company with an ISMS that has been developed by experts and meets the highest standards.
What benefits does an ISMS offer?
4conform ENTERPRISE ISMS is used specifically to make managing your information security easier and more efficient. It serves as a central platform to support processes relating to information security, risk and compliance management.
What our customers in logistics say
“As a manufacturer of biometric access solutions, we have high requirements for our information security. With its clever interface, ease of use and lean infrastructure, 4conform Enterprise helps us to develop our company towards compliance with BSI baseline protection and ISO 27001. An ISMS that even an SME can operate well.”
ekey biometric systems GmbH,
Manufacturer of biometric access solutions

Data protection
How can our DSMS help you?
For SMEs, a comprehensive data protection management system (DSMS) is crucial to protect sensitive and personal data. 4conform also offers its customers such a system. Our ENTERPRISE DSMS ensures that all data processing procedures comply with legal requirements and that the privacy of data subjects is protected.
A DSMS helps to strengthen the trust of customers and partners and minimize legal risks. By implementing a DSMS, SMEs can not only ensure compliance, but also protect their reputation and build long-term business relationships.
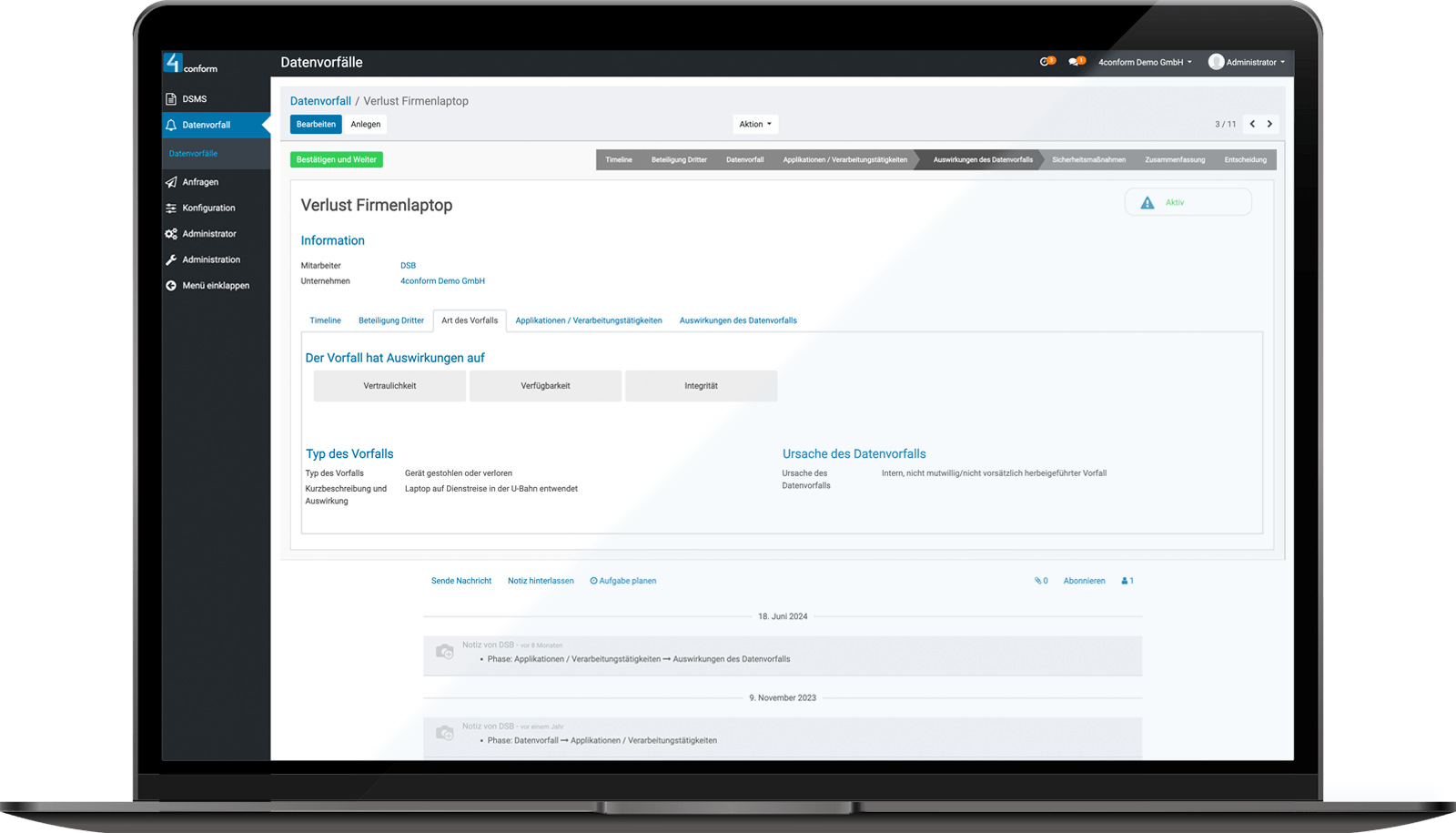
Process data incidents easily and in compliance with the law in ENTERPRISE DSMS.
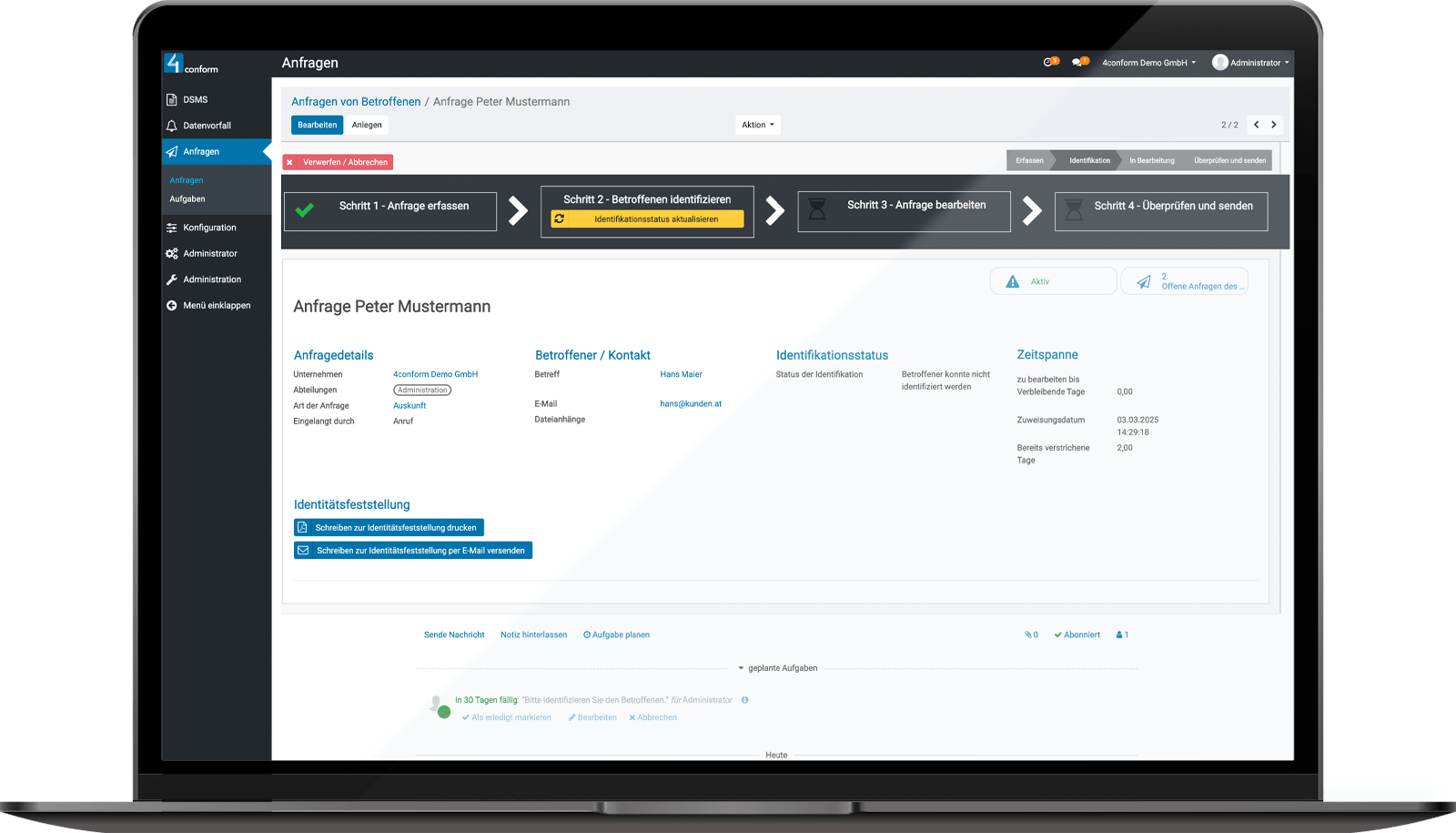
Manage and process your data subject requests in accordance with the legal requirements.
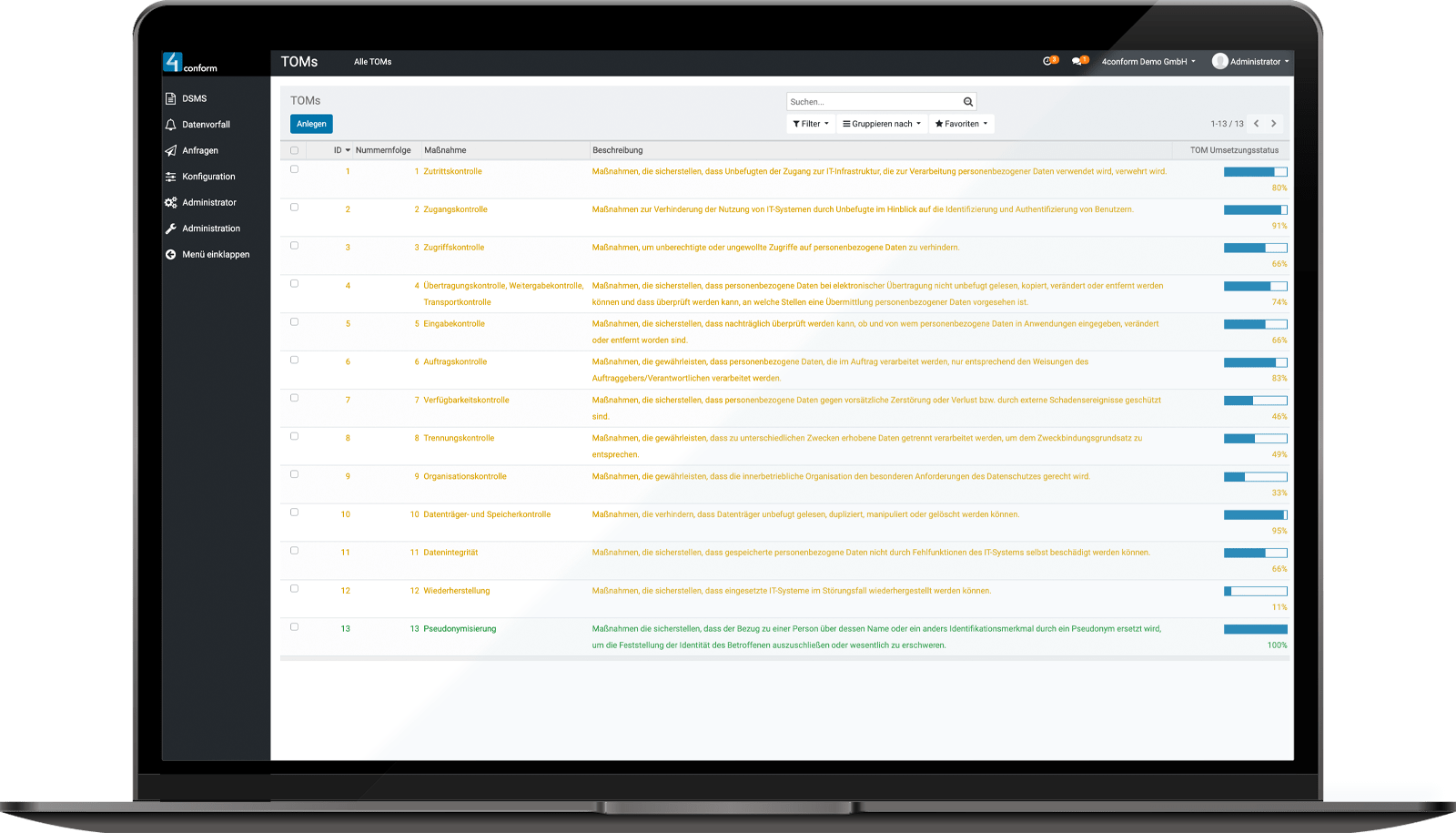
Map out your technical and organizational measures.
DSMS Live
Take a look at our DSMS in action
Book a demo now and find out how you can efficiently ensure the protection of sensitive data and meet legal requirements. In your demo appointment, we will show you how easy it is to integrate data protection into your company. Save your appointment and start into a more secure future!

What benefits does a DSMS offer?
Our ENTERPRISE DSMS software (data protection management system) is primarily used to ensure the protection and management of data in an organization. It focuses on compliance with data protection and data security regulations and the prevention of data breaches.
“NIS2 is not just a burden, but also an opportunity. By preparing for NIS2, we are optimizing our IT processes and reducing risks. This makes us more efficient, more resilient and more attractive to business partners.”

Full security with 4conform
Information and data security is a complex topic. But it doesn’t have to be complicated. Get to know our smart GRC and information security solutions and arrange a non-binding initial consultation.












