Risk-free
Risk management
Minimize your data risks and maximize your cyber security at the same time. With a powerful and user-friendly ISMS, specially developed for the requirements of modern companies. See for yourself.
Information security
[In-for-ma-ti-on-se-cu-ri-ty], the; noun
Information security refers to the protection of information from unauthorized access, use, disclosure, disruption, modification or destruction. It includes measures and strategies to ensure that information remains confidential, integer and available.
ISO 27001 is an internationally recognized standard for information security management systems (ISMS). It offers a systematic approach to implementing, maintaining and improving information security within an organization.
Confidentiality
Ensuring that information is only accessible to authorized persons or systems. This protects sensitive data from unauthorized access.
Integrity
Ensuring that information is accurate, complete and protected from unauthorized or unintentional modification. This ensures that data remains reliable and accurate.
Availability
Ensuring that authorized users can access the required information at all times. This includes measures to ensure business continuity and minimize downtime.
With ENTERPRISE ISMS, stay on top of everything
4conform supports corporate information security officers (CISOs) in identifying the risk situation, assessing the risks and closing security gaps through targeted action management.

Enterprise ISMS
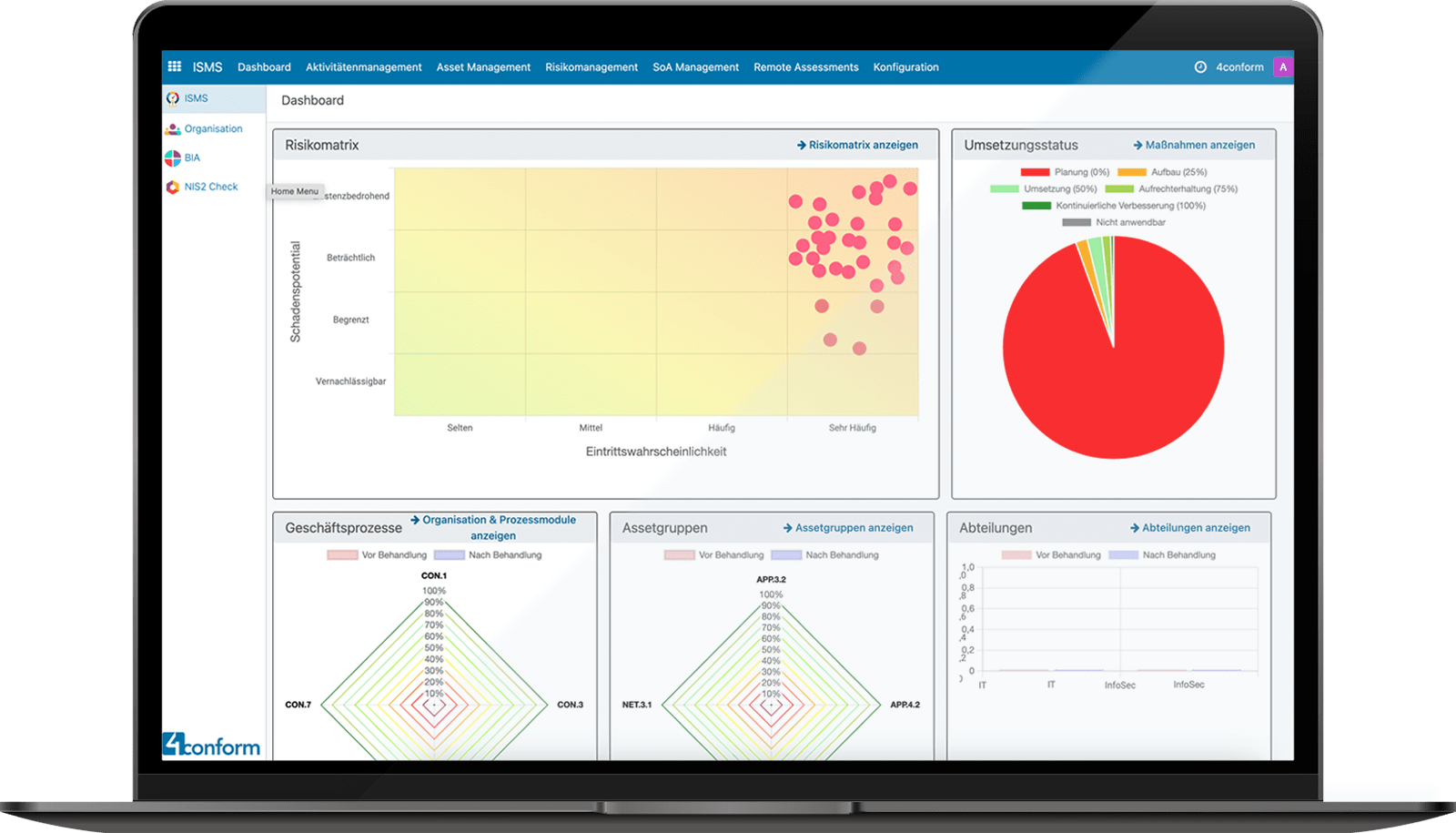
With 4conform ENTERPRISE ISMS, CISOs always have a complete overview of all tasks and can call up any report in a matter of seconds. The assessment is not only carried out at process module level, but also at asset group and asset level – a hybrid solution that combines flexibility and precision. Automated workflows, distributed risk assessments and easy handling of daily process activities are just some of the highlights. This saves you valuable time with minimal effort.
As soon as the documentation of your risks and measures has been completed, all other modules automatically access the entered data. Defined algorithms and an intelligent action management system significantly reduce the work involved in information security, allowing you to concentrate on strategic decisions.
Further advantages at a glance
Risk treatment
Define risk owners and risk treatment options based on the current situation and assign security measures and tasks with one click.
Security according to ISO/IEC 27001
4conform ISMS offers standard-compliant management in accordance with ISO/IEC 27001:2022 in order to consider security and data protection risks together and derive measures semi-automatically.
Defined measures
The automatic assignment of BSI measures to hazards and assets is available to you in the ISMS. Save yourself the definition and research – individually customizable!
Maximum knowledge with minimum effort
We offer you maximum knowledge with minimum effort by using the proven building blocks and comprehensive knowledge from BSI IT-Grundschutz. This integration enables efficient and effective security solutions.
In-depth risk assessment thanks to BSI
By linking assets with measures and hazards as well as detailed risk assessment at departmental level, we offer an in-depth view of corporate risks. We keep these building blocks up to date at all times to give you a competitive advantage.
Statement of Applicability
Thanks to the Statement of Applicability, or SoA for short, directly in the software, you always have an overview. Thanks to mapping to ISO 27001:2022 and other standards such as BSI, NIS, Kritis etc.
Organization & access concept
Define roles and rights for safety officers or the entire workforce.
Automated reporting
Our software automatically creates risk reports or supports you in creating individual reports with the reporting generator.
Maturity assessment
Use the expert mode for self-assessments or let the software evaluate the maturity level by asking specific questions.
Automated risk assessment
Our automated assessment methodology enables specialist departments to assess information security risks in a simple and distributed manner. The CISO immediately receives an up-to-date and meaningful risk situation picture.
Asset management
Import, classify and evaluate your assets. You can manage and allocate them and identify and improve the associated processes, risks and measures.
Asset-based risk assessment
Evaluate risks in business processes and IT assets using the BSI modules “Organization & Processes” and “Asset Groups”. Always keep an eye on criticality and damage potential.
Ready for an initial consultation?
A short conversation has never hurt anyone. The initial consultation is non-binding and serves to get to know you and your needs better.
ISMS Live
Take a look at our ISMS in action
As the person in charge of information security, one of the challenges you face is managing risks quickly and efficiently without losing sight of the big picture.
This is exactly where we come in – not at some point, but now. See for yourself in our short video or the guided tour on Webinar Geek.












